
Social Media Security – Tips for Safe Social Media Management
Opportunities and risks are often closely linked. Social media marketing offers great opportunities to interact with your target audience, raise brand awareness, and find new customers. But it can also become a security risk. For example, if the wrong people gain access to your accounts, the consequences can be devastating.
Companies need to take targeted measures to ensure secure social media management to avoid serious mishaps. Here you can find out what these are and how to best proceed. We will also discuss how to find secure social media tools and what to look out for when working with service providers.
The most common dangers in social media marketing
The following are among the biggest security risks in social media:
Phishing
You are probably familiar with the term phishing in the context of e-mails. The principle is the same on social media, only the means differ: on Instagram, LinkedIn, and the like, fraudsters use direct messages, posts, or comments to steal sensitive data or infect systems. For example, criminals pretend to be a company executive in WhatsApp messages and trick users into clicking on a link that downloads malware or instructs them to carry out transactions. Not every quiz is as harmless as it seems at first glance either.
Hacker attacks on accounts
In hacker attacks, attackers take over company accounts or advertising accounts. They then post content or send phishing messages. This affects not only companies but also public authorities. In 2023, for example, attackers took over the Instagram account of the city of Bielefeld for several hours.
Incidentally, according to a survey, social media accounts are most frequently hacked in Germany, even more so than email accounts.
Insufficient data protection settings
Companies can access valuable data via social media. This is even the case when social media accounts are linked to websites. If companies do not want to risk heavy fines, they must comply with the applicable data protection regulations when handling this data, meaning GDPR. Because these are often anything but easy to understand, we recommend that you seek legal advice. This way you are on the safe side.
Human error
Malicious intent is one thing. Equally important as a cause of security breaches on social media is negligent or faulty behavior. This starts with easy-to-crack passwords. Unsecured cell phones increase the risk of unauthorized access to passwords, and anyone who is mentally planning the end of the day may quickly click on a spam link or publish sensitive data.
Fraudulent accounts
According to its figures, LinkedIn took action against 70.1 million fake accounts between January and June 2024 alone. Fake accounts of companies or employees are often used to persuade people to disclose confidential information or take other actions.
FC Barcelona’s Twitter accounts have been hacked, which is why messages from outside our club have appeared, and which have been reported and deleted. The tweets were made through a third-party tool for data analytics.
— FC Barcelona (@FCBarcelona) February 15, 2020
AI tools make phishing and hacking attacks on social media even more dangerous. With the help of AI, it is easier to create fake messages and accounts that look deceptively genuine in a short time. Fraudsters can effectively imitate the tone of voice of individuals and create flawless texts in different languages.
Best practices for social media security
1. The basics: set up social media guidelines
One moment of inattention and it’s already happened. In many cases, the greatest danger does not come from outside. Instead, your colleagues can cause a shitstorm with careless statements in a company account or download malware with a spontaneous click on a link.
The basis for social media security is therefore a social media policy that regulates how social media is used in your company.
Among other things, it should cover the following content:
- who is responsible for social media in the company,
- how to deal with copyrighted content,
- how to deal with confidential content,
- guidelines for personal use of social media,
- what activities to avoid on social media,
- guidelines for communicating about the company,
- tips for recognizing threats,
- measures to take in a crisis.
Important: Make sure that social media guidelines don’t just exist somewhere in a real or digital drawer, but are also read by all employees. This means, for example, that you actively draw them to the attention of new additions to the team.
2. Clearly define roles and responsibilities
Clear processes and responsibilities help to avoid incidents. Define in your team or company who is responsible for what in relation to social media, which approval processes content must go through, and who is the point of contact in the event of a crisis.
Approval processes are important to avoid missteps like the following:
Uh, hey @cynetjobs – what’s with this?
— Helena (@misshelenasue) April 27, 2019
Your job listing for a mid-senior level business development position’s top qualification is “Preferably Caucasian”
How could you POSSIBLY think that’s okay? pic.twitter.com/DPWzpgXqqE
3. Centralized Access Control
With a social media management tool like Swat.io, you can assign user roles to which permissions are attached. This means that while some people can edit tickets and/or posts at any time, others are only allowed to view content assigned to them.
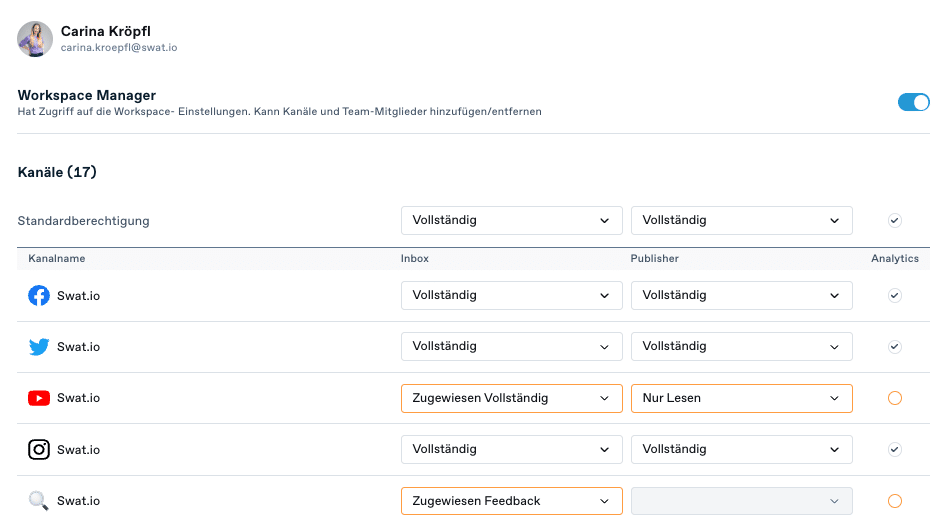
Tip: Always make sure to appoint at least two admins in case one of them is unavailable.
4. Define secure passwords
Sie sehen gerade einen Platzhalterinhalt von Standard. Um auf den eigentlichen Inhalt zuzugreifen, klicken Sie auf den Button unten. Bitte beachten Sie, dass dabei Daten an Drittanbieter weitergegeben werden.
Weitere InformationenMost people know that your birthdate is not a particularly good choice for protecting sensitive information. But many other passwords are also easy for hackers to crack.
In principle, the following applies to secure passwords:
- They consist of at least 8 characters.
- These include upper and lower case letters, numbers, and special characters.
- Under no circumstances should users use the same password for multiple logins.
- Storing passwords on a computer is also not a good idea.
- Change passwords regularly to further increase security.
You can integrate guidelines for secure passwords into your company’s social media guidelines. A password manager, for example, makes it easier to handle passwords.
By the way: If you change your password on a social media platform, you may need to re-link the channel in your social media tool. Swat.io will notify you in this case.
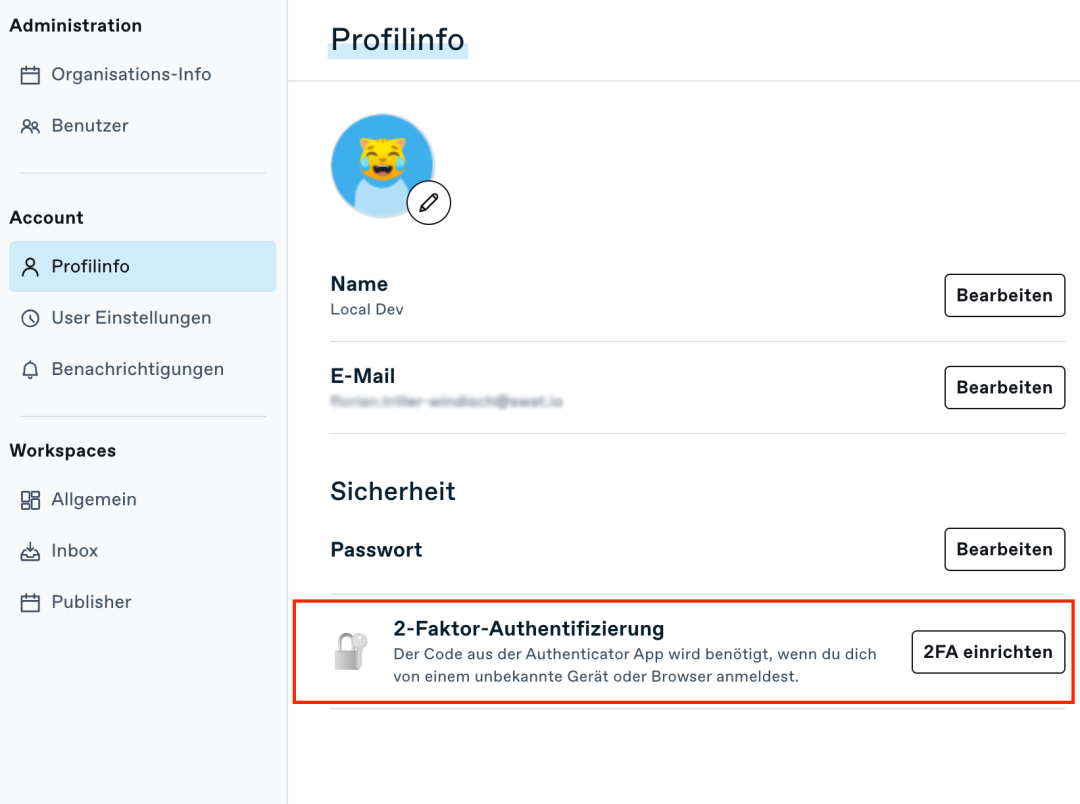
5. Use 2-factor authentication
Even better than a good password is something called two-factor authentication.
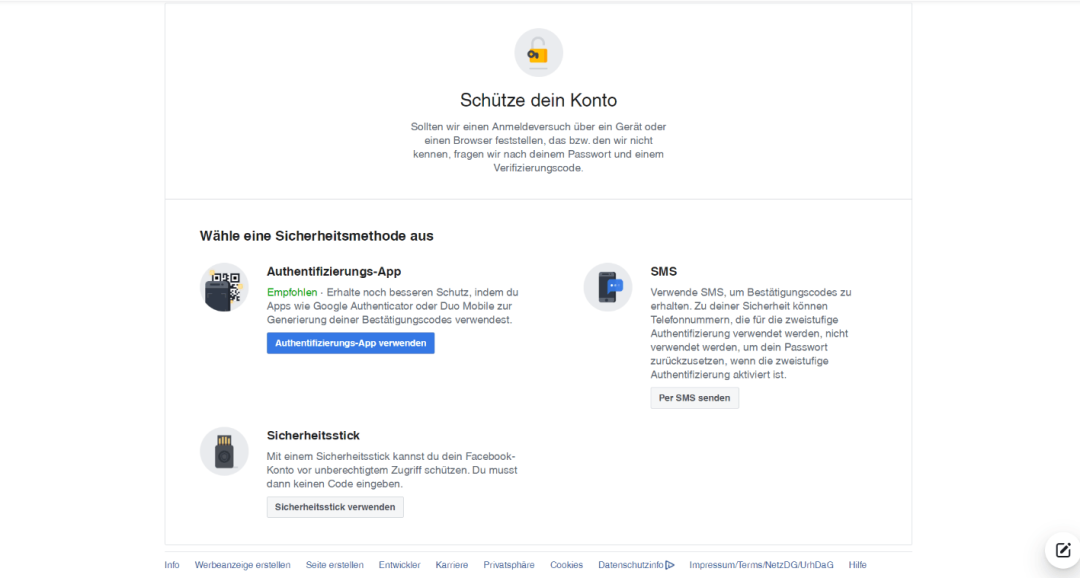
This means that in addition to a password, a person needs a second “key”, for example, a code sent to their smartphone or an authenticator app. This may sound complicated, but it is very easy to set up and takes hardly any more time than a single-factor login. The big advantage of this is that even if a password is cracked, attackers cannot access the account in question because they also need the second key. This makes two-factor authentication a very easy way to increase account security.
Many major networks allow you to set up two-factor authentication. Facebook, for example, offers several options for this:
With Swat.io you can also be sure that no unauthorized persons have access to company accounts. You can find 2-factor authentication for your account in the settings. If you are an admin, you can also make 2FA mandatory for everyone on the team. You can choose an app of your choice to set up authentication.
6. Get your accounts certified
A little blue (or other colored) checkmark doesn’t just look nice. It also protects against fake accounts. Social media platforms offer you various options for having your profile verified. This is proof of authenticity and, depending on the platform, has other advantages, such as better support.
Social media verification is increasingly subject to a fee, but it does bring clear security benefits.
7. Use social listening
Social monitoring or social listening not only tells you more about current trends and the image of your brand or products. It also helps you find out faster if someone is misusing your company’s name for criminal purposes or phishing attacks.
We’re sorry for any confusion as we’re in no way affiliated with the social account or giveaways mentioned. We always recommend exercising caution if asked for any of your personal information online. We invite you to follow our verified social profiles for our promotions!
— Bath & Body Works (@bathbodyworks) April 17, 2020
To detect threats, you can use special social media monitoring tools or social media management tools with monitoring.
Tip:
Social media is also a good way to inform your communities about phishing attempts on other channels.
You are currently viewing a placeholder content from Facebook. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information8. Keep up to date on new threats
Threats in the IT sector change quickly. To ensure that your company is not defenseless against attacks, keep up to date on new security vulnerabilities. With the help of internal or external IT specialists and relevant media, keep up to date on the latest developments in social media security.
9. Raise employee awareness and hold security training
Employees are often unaware of the dangers lurking in social networks.
On the one hand, you can raise awareness utilizing the social media guidelines already mentioned, which are regularly revised. On the other hand, it is worthwhile for social media teams to complete training on security topics.
These are particularly effective if they
- are interactive and varied,
- include practical exercises (for example, phishing attacks can be simulated),
- take place in small chunks,
- are easily accessible and
- videos and other modern media.
You can also make sure the topic doesn’t get forgotten by bringing it up in meetings from time to time.
10. Tips for working securely with third parties
Do you work with external service providers such as graphic designers or copywriters in social media marketing?
Then take the following security measures:
- Contractual provisions and non-disclosure agreements: Integrate clear provisions on data protection, data security, and responsibilities into contracts. An NDA (non-disclosure agreement) is also useful. Such a confidentiality agreement defines which data is considered confidential. Service providers agree not to pass this on to third parties or use it for other purposes. An NDA also defines the legal consequences of violations.
- Access rights and permissions: Only grant the access rights for your social media accounts and tools that are absolutely necessary. If possible, use guest access or user roles with limited rights.
- Data protection compliance: Make sure that service providers comply with data protection guidelines such as the GDPR, especially when customer data is being processed.
11. Coordination with other departments
Optimal security in social media management is the result of the interaction of different people and departments. The IT team can keep you up to date on new threats. This is crucial because the strategies and tools of cybercriminals are constantly evolving. A legal department is the right point of contact for issues such as data protection.
Tip: If there are no lawyers in your organization, you can call on external experts on an ad hoc basis.
12. Use security tools for social media
Some tools can help you to ensure more social media security. These include the aforementioned password manager. This serves as a “vault” for passwords that you can’t remember and shouldn’t be stored in a Word file or on a notepad. There are also social media scanners, for example, that scan profiles for dangerous links and the like.
With https://haveibeenpwned.com/, you can quickly find out whether an email address or phone number was part of a larger data leak. The tool https://www.experte.de/email-check offers similar data on 400 leaks in German.
The cybersecurity platform ZeroFOX warns you about posts with malicious links in your accounts and about fake accounts posing as your company.
Tips for choosing secure social media tools
Sie sehen gerade einen Platzhalterinhalt von Standard. Um auf den eigentlichen Inhalt zuzugreifen, klicken Sie auf den Button unten. Bitte beachten Sie, dass dabei Daten an Drittanbieter weitergegeben werden.
Weitere InformationenAs the center and hub for your team’s social media activities, your social media management tool plays a key role. That’s why it can also become a gateway for hackers or lead to serious mistakes.
But how do you recognize secure social media tools?
Pay particular attention to the following features:
- 2-factor authentication: Two-factor authentication ensures security even if hackers have managed to obtain login data for your tool.
- Server and company location: If personal data is processed, you should check whether it is stored in secure countries. The company’s location affects the legal situation.
- Transparent documentation: Check whether the tool makes legal information easily accessible. Plus points are awarded if changes can be easily traced.
- Activity log: With an activity log in the social media tool, you can track all changes, releases, etc., and assign them to a person.
- Permission features: The more precisely you can assign permissions for individual tasks, the better. This reduces the risk of someone accidentally making changes or posting too early.
- Deletion routines: If you can set frequencies for when personal data is deleted, it will be easier for you to comply with the requirements of the General Data Protection Regulation (GDPR).
- Secure data transfers and backups: Make sure that your data is transferred securely and that the tool creates backups so that sensitive data is not lost in an emergency.
Certifications help with the selection
Recognized certifications are proof of verified security. If a tool provider is ISO 27001 certified, for example, their information security measures are regularly scrutinized by independent auditors. The company only receives a certificate if it meets these high requirements.
Good to know: ISO 27001 is an internationally recognized standard for information security management systems (ISMS). It defines measures that companies must take to ensure the confidentiality, integrity, and availability of information. These include thorough risk management, security controls, and regular employee training. Another requirement for certification is that companies consistently develop and improve their information security management. This is how they keep pace with new threats.
With Swat.io you are safe on social media. Because we are ISO 27001 certified. Read on to find out what this means for you and what additional measures we take to ensure security!
What to do if an account has been hacked
There are several ways in which a social media account being hacked can be revealed:
- Posts appear on your timeline or profile that do not come from your team.
- You receive notifications about a login from a new device or new software.
- You learn of changes to your account, such as a password change.
- You and your colleagues can no longer log in to your account.
You must take these warnings seriously and react:
- Use recovery options.
- Change the password.
- Remove third-party content immediately.
If this is not possible, for example because you can no longer access your account, notify support as soon as possible.
Important: With a social media management tool, you can still post in such a case until the set tokens have expired. Depending on the tool and platform, you can even delete posts that have been posted on the platform using the tool.
Social media security requires constant attention
Establishing security in social media management is a long-term task. It requires constantly revising guidelines, reviewing previous measures, and taking additional ones. Above all, it is advisable to keep the topic in mind during day-to-day business.
This may seem exhausting at first, but it pays off. Because social media security protects you and your community from serious consequences.
Swat.io not only makes your social media marketing easier with features like a clear editorial plan and a central ticket inbox. Two-factor authentication, social media monitoring, and customized permissions ensure social media security in your daily work. Start a free trial now!
 12. February 2025
12. February 2025 








